Ansible is an open-source software provisioning, configuration management, and application-deployment tool. It is one of the most powerful enough to automate complex multi-tier IT application environments. To know more about Ansible you can go through this post >> What is Ansible and How it is so Powerful?
How to set Ansible?
Aws Apache Web Server Download
I have already created a post where you can learn how to set up the ansible successfully and we also troubleshoot some of the problems. Incase if there any error occurred you can comment down below or can connect with me over the social media handle as well. To know the setup part you can go through this post >> How to setup Ansible in RHEL8?
To set up a LAMP web server on Amazon Linux AMI, see Tutorial: Install a LAMP web server on the Amazon Linux AMI. Now that your instance is current, you can install the Apache web server, MariaDB, and PHP software packages. Use the yum install command to install multiple software packages and all related dependencies at the same time.
Task Description
- How to Setup an Apache Web Server with AWS EC2 Instance 2020Git For Windows:an Apache Web Server with PHP:https:/.
- How to Setup an Apache Web Server with AWS EC2 Instance 2020Git For Windows:an Apache Web Server with PHP:https:/.
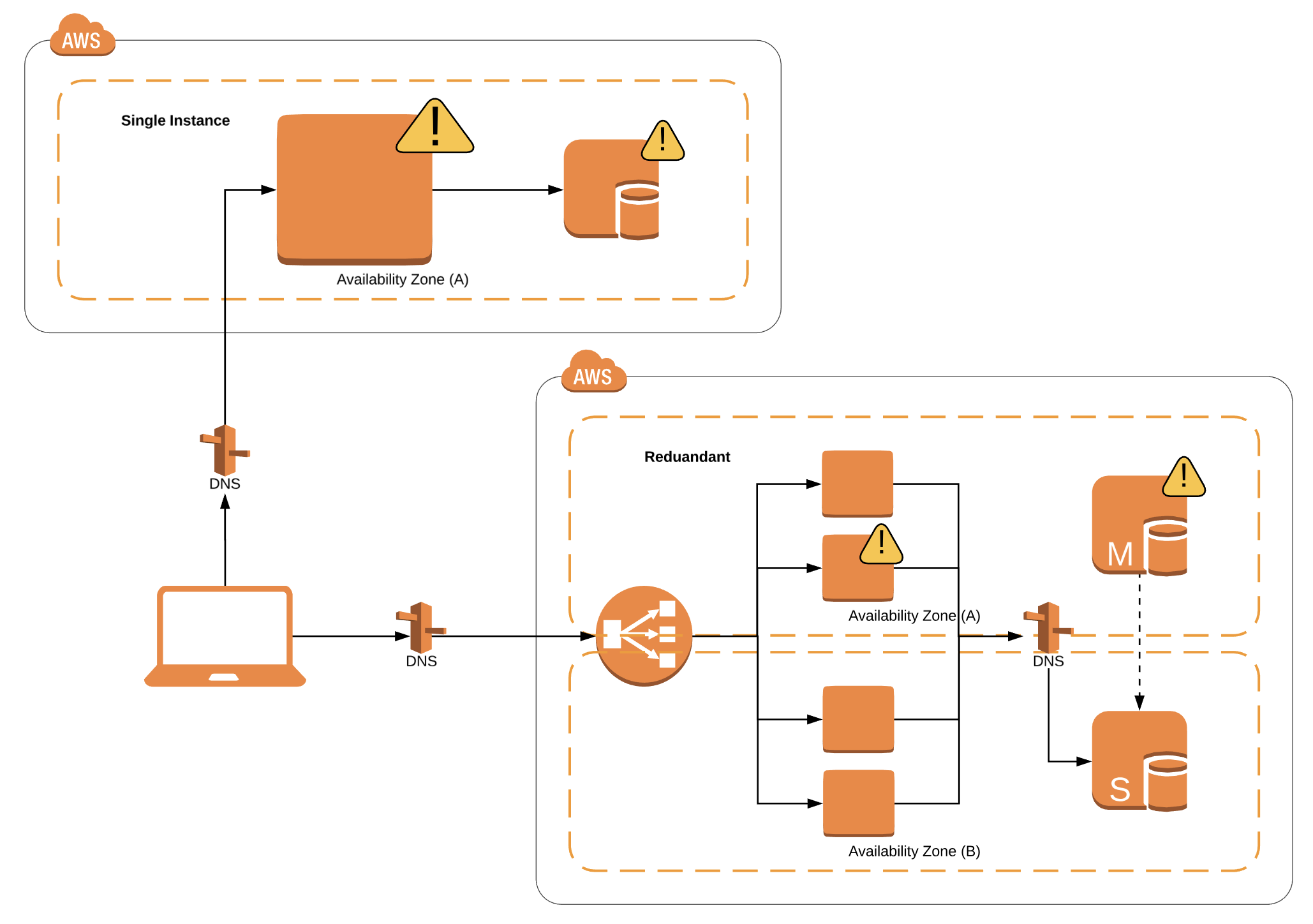
We are going to create one Ansible playbook that will set the following set up:
- Provision an EC2 instance on AWS.
- Fetch the public IP using the EC2 dynamic inventory concept.
- Configure webserver.
Prerequisite
Before going further to solve the task we need some additional setup. I already installed the Ansible on my RHEL8 system.

- We need one IAM role in AWS so that Ansible can log in and do the required set up.
- Boto and Boto3 library of python. To install the library we can use “pip install boto” and “pip install boto3“. This will install the boto library and that library will automatically source the AWS API credential for EC2 instances and IAM roles.
- To provide the AWS credential we have multiple ways and one of them is by providing through the below command
- Ansible dynamic inventory file. Now you need two files EC2.py script and the EC2.ini config file. The EC2.py is written using the Boto EC2 library and will query AWS for your running Amazon EC2 instances. The EC2.ini file is the config file for EC2.py and can be used to limit the scope of Ansible’s reach. You can specify the regions, instance tags, or roles that the EC2.py script will find.

In order to get the above files, you can follow below link
To download this through command you can use wget<url>. Now we have to make it executable and to do so we can use below command
As for the Linux user there, one more thing I have to change is in the ec2.py file where we have to make some changes in the header path of the python interpreter. Earlier it is #!usr/bin/python and we have to convert it as #!usr/bin/python3.
now we have to add the location of above both files in our configuration as above our inventory file.
Let’s come to our task. Before going to the task I would like to tell you that in this task i am going to use some technical terms of AWS and in case you don’t know you can go through my AWS posts.
Code
Provision an EC2 instance on AWS
To provision this I created a role and named that as task2
For creating the key pair for the task through the below code and also saved the key locally.
To create the security group
To create the EC2 instance
This will launch an instance over AWS and also set the inventory dynamically in our inventory file of Ansible. Our first and second step is done now we will set the webserver.
Configuring Webserver
To configure this I created another role name as web
To install the apache web server we need python3 so we install that first
Now to launch the apache webserver we will use
This will install the web server and copy the code from the url and start the httpd service.

Now to run both the roles I created one playbook aws.yml
Now after running this our whole set up will be ready and here is some result of that.
To get the whole code you can go through Github >> https://github.com/anubhavsinghgtm/aws-ansible-dynamic-inventory
In case of any query, you can comment down below or connect with me over.
VISIT OUR WEBSITE BRIGHTERBEES FOR MORE INTERESTING STUFFS ABOUT LEARNING.
IF YOU WANT TO KNOW ABOUt DATA SCIENCE click here.
Download microsoft office 2011 for mac. Thank you
Related
In this article I cover how to install Apache HTTP Server into Ubuntu 18.04 LTS.
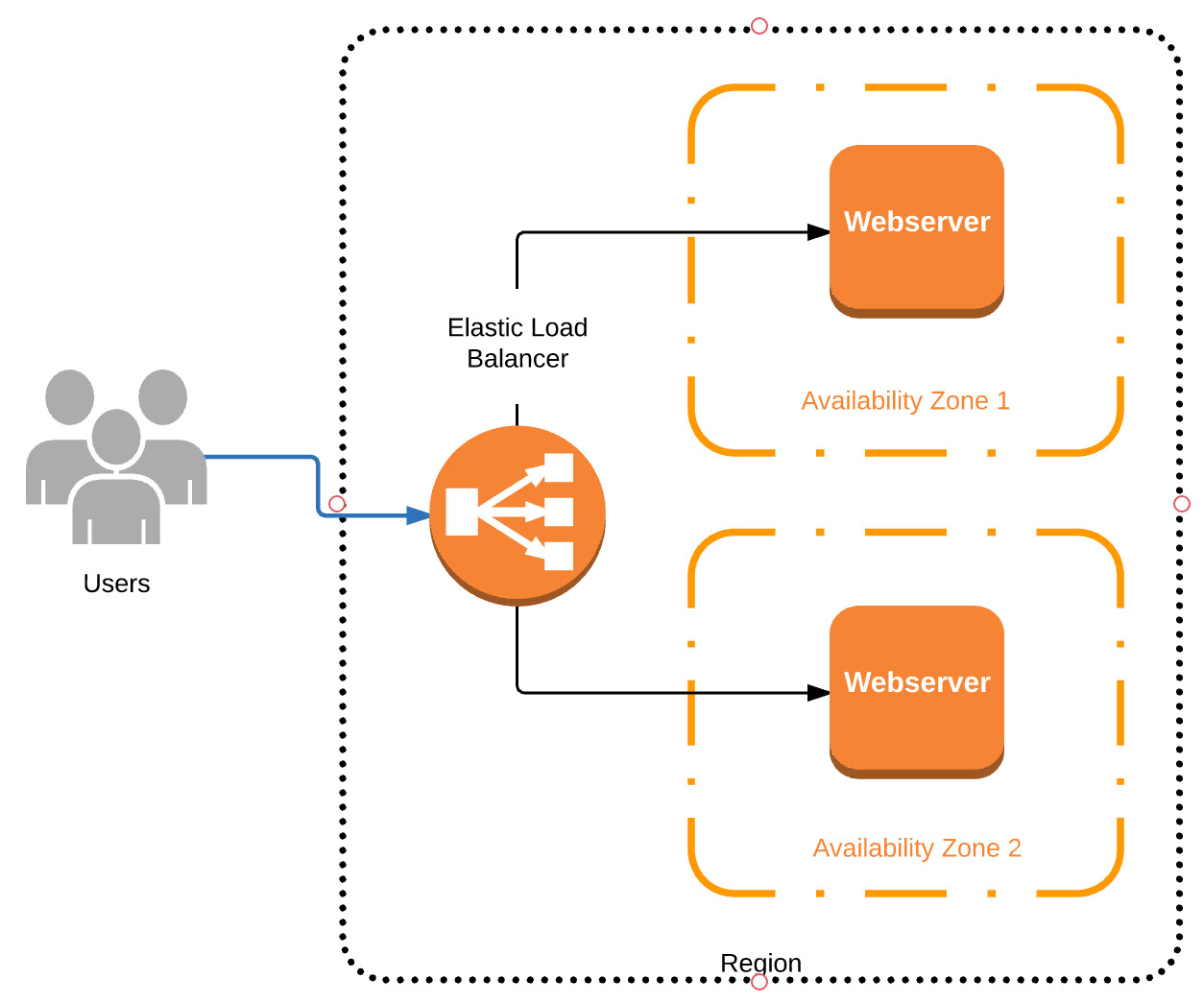
This article is part 2 of a series on how to create a Tomcat server in AWS. In part 1 we created an Ubuntu 18.04 LTS server in AWS EC2. We now add Apache HTTP Server as a front-end for Tomcat.
Motivations
When discussing reasons why you should have an Apache Web Server as a front-end to Tomcat, people usually talk about load balancing, fast serving of static content, enhanced security and so forth. These are all good reasons. My main reason though is that I want to serve custom-branded pages even when Tomcat is down.
Installation
Apache is a very mature software. You can make life marginally more difficult for yourself by trying to install a specific version. Or you can just take the easy option and install the version packaged with the Ubuntu. I choose to embrace the lazy pragmatist within, so I’ve gone for the latter.
This installs Apache to the /etc/apache2 directory. You can check what version is installed using:
Apache Web Server Aws
With Apache installed, you can immediately test it by confirming that its default page is accessible at the Public IP or domain name of your server.
Configuration
Remove Default Virtual Host
OK, we’ve seen the default Apache web page for long enough. Time to get rid of it. If you actually took the time to read the default page, the following command will make sense.
Static Content
We need to create a directory to hold the static content for our site. It seems the Apache convention is to make a sub-directory in /var/www
What you will want to put in here is entirely up to you. For the purposes of my example, I’m going to put just one HTML file.
With trivial contents.
For a real site, you would build a rather more impressive page.
Proxy AJP
Although Tomcat isn’t installed yet, let’s jump right in and enable Apache’s Proxy AJP module. We will use it to forward requests to Tomcat in the next article.
Virtual Host
Now we need to create a so-called virtual host for our website. For the purposes of this post, we’ll cover just a HTTP (port 80) virtual host file. HTTPS (port 443) is covered later in the series.
I elect to create a common file that can be shared, eventually, by both the HTTP and HTTPS virtual host configurations.
With contents:
The DocumentRoot element sets the root to the static content directory we created earlier.
The ErrorLog and CustomLog elements can be almost anything you want. What I have done is quite conventional.
I have told Apache to pass all requests through to Tomcat, except for requests to /error.html. All requests to Tomcat, and responses from it, are handled by the Proxy AJP module we enabled earlier.
If Tomcat is down (or not installed), we expect the AJP request to return a 503 (Service Unavailable). In that case, Apache will serve /error.html.
With the common file in place, we can now create the HTTP (port 80) virtual host file.
With contents:
The virtual host can then be enabled.
Instruct Apache to reload its settings.
And if we surf now to the Public IP or domain name, voila, we see the error page. This is because Tomcat is not yet installed, so all the Proxy AJP forwards fail. Therefore we will get this error page served for any URI.
Please remember, you can make your custom error document look a lot better than my trivial example.
Hardening
In the references, I include links to guides on how to harden an Apache installation. Most of the advice is already incorporated in a default installation of Apache Web Server in Ubuntu. What follows is a couple of steps I recommend.
Server Signature
If we didn’t have a custom error document, Apache would serve the following page when Tomcat was down (or not installed). This would reveal details, such as server version, that can give an attacker a head start.
To get rid of this signature from default pages, we need to edit the security configuration.
And disable the the ServerSignature.
Server Tokens
Even with the ServerSignature off, responses from Apache still report the server version in the HTTP response header. This can be viewed using Firefox or Chrome web development tools.
To remove this, again edit the security configuration.
And set ServerTokens to the least revealing setting.
References
